Openings with Novoitindia
Dear Candidate,
We do have a suitable opening matching to your profile. Please find the JD below
Particulars of the Vacancy
Exp :3 to 6yrs
SAP Security consultant
Job type: Full-time Regular
Work city: Bangalore, Mumbai & Kolkatta
Education: 16 yrs
Note: who are working on permanent pay roll only they can apply.
Interested candidates may send in your resumes to sujatha@novoitindia.com
Also we kindly request you to forward the above opportunity to your friends / refer some of your friends or colleagues who are seeking change in their career.
NOTE: We apologize, if any inconvenience is caused or this job opening is irrelevant / not of interest to you and request you to ignore this mail.
Appreciate your positive response ASAP.
Thanks & Regards,
Sujatha
Sr.Technical Recruiter
Novo IT Consultants & Solutions Pvt. Ltd.,
Innovative Minds
No.143, 1st Floor, 10th 'A' Main,
5th Cross, 1st Block, Jayanagar,
Bangalore - 560 011 (India)
Web : www.novoitindia.com
Email: sujatha@novoitindia.com
Tele-Fax : 91-80-40951060
Mob: 9844651492
Pyramid IT Consulting India-SEI Client
Dear Candidate,
Job Greeting!!!
At Present we have Urgent Permanent Job Opening in SAP Security with Our Client SEI CMMI Level 5 !!!
This demand is Open till 19th December,2012 (Wednesday )
Required Skill:
SAP Security
Candidate must have 3+ Yrs experience in SAP Security
Candidate must be currently working with SEI CMMI Level 5 /Tier 1 Organisation as a Permanent basis.
Note : Candidate Based out @ Mumbai, Need to come for Interview @ Pune Location
Candidate Based out @ Delhi NCR, Need to Come for Interview @ Gurgaon Location
Work Location: Mumbai /Kolkata,
Incase you preference is Mumbai. then you should have 4+ Yrs of Experience in SAP Security
Educational Qualification
Consistent academics records from class X onwards
Graduation ( Full Time)/MBA / MCA / BE / BTech / MCA / M.Tech / Any Post Graduation or Candidate Must have 16+ Yrs of Educational Qualification
In case you are seriously interested for the same & can join within 1 or 2 months (Max), please send your resume as a Word Attachment along with following details.
Total & Relevant Experience:
Current and Expected CTC ( In Fig):
Notice Period
Contractual /Permanent
Current and Preferred Location & Notice Period: Date of Birth:
Current Address with PIN Code
Thanks and Regards
Shantpriya Chandra
Pyramid IT Consulting India
8447428046
Job Greeting!!!
At Present we have Urgent Permanent Job Opening in SAP Security with Our Client SEI CMMI Level 5 !!!
This demand is Open till 19th December,2012 (Wednesday )
Required Skill:
SAP Security
Candidate must have 3+ Yrs experience in SAP Security
Candidate must be currently working with SEI CMMI Level 5 /Tier 1 Organisation as a Permanent basis.
Note : Candidate Based out @ Mumbai, Need to come for Interview @ Pune Location
Candidate Based out @ Delhi NCR, Need to Come for Interview @ Gurgaon Location
Work Location: Mumbai /Kolkata,
Incase you preference is Mumbai. then you should have 4+ Yrs of Experience in SAP Security
Educational Qualification
Consistent academics records from class X onwards
Graduation ( Full Time)/MBA / MCA / BE / BTech / MCA / M.Tech / Any Post Graduation or Candidate Must have 16+ Yrs of Educational Qualification
In case you are seriously interested for the same & can join within 1 or 2 months (Max), please send your resume as a Word Attachment along with following details.
Total & Relevant Experience:
Current and Expected CTC ( In Fig):
Notice Period
Contractual /Permanent
Current and Preferred Location & Notice Period: Date of Birth:
Current Address with PIN Code
Thanks and Regards
Shantpriya Chandra
Pyramid IT Consulting India
8447428046
Openings with Synova India-NTT Data
Greetings from Synova India
SYNOVA is a technology enterprise established in MI - USA in the year 1998. We offer enterprise software services to medium and large organizations. We have our presence in the US, Brazil, Hong Kong, China, Singapore and in India. We are a $100 million turnover company with about 2500 employees working with us. SYNOVA India is focused on enterprise applications, mobile applications and cloud enablement. SYNOVA has deployed several thousand top notch technical professionals to many fortune 500 companies in India. Some of our key clients are IBM, Wipro etc.http://www.synovainc.com/
Skill: SAP Security
Experience: 4.0 to 5.0
Client: NTT Data (Keane India) http://www.nttdata.com/global/
Job Mode: Permanent employee in Synova India.
Client Work Location: Hyderabad & Bangalore
Note: Candidate must ready to join within 15 to 20 days not more than that.
If you are interested please sent to your update CV along with as given below details...
Current CTC:
Expected CTC:
Notice:
DOB:
SYNOVA is a technology enterprise established in MI - USA in the year 1998. We offer enterprise software services to medium and large organizations. We have our presence in the US, Brazil, Hong Kong, China, Singapore and in India. We are a $100 million turnover company with about 2500 employees working with us. SYNOVA India is focused on enterprise applications, mobile applications and cloud enablement. SYNOVA has deployed several thousand top notch technical professionals to many fortune 500 companies in India. Some of our key clients are IBM, Wipro etc.http://www.synovainc.com/
Skill: SAP Security
Experience: 4.0 to 5.0
Client: NTT Data (Keane India) http://www.nttdata.com/global/
Job Mode: Permanent employee in Synova India.
Client Work Location: Hyderabad & Bangalore
Note: Candidate must ready to join within 15 to 20 days not more than that.
If you are interested please sent to your update CV along with as given below details...
Current CTC:
Expected CTC:
Notice:
DOB:
Job Openings with IBM India
Dear Candidates,
Greetings to all !!!
Excellent Openings with IBM for "SAP Security"
Job description:
SAP Security
Exp - 3 - 6 years
Job Location: Kolkata & Mumbai
Please send your updated profile with the below details ASAP.
Full Name :
Current Organisation (Permanent) :
Current Designation:
Total Exp:
Rev Exp:
Current CTC :
Expected CTC :
Joining Notice :
Prefered Job role :
Date Of Birth :
Mail id :
Alt mail id :
Pan Card No:
Reference of your friends and colleagues into the same.
Kindly consider this as matter most urgent !!!
Note: It"s a very urgent requirement, so kindly send across your profile ASAP so that I can go ahead with the further process.
HR Security Authorizations
Introduction on Authorizations
· Authorization
objects enable complex checks of an authorization, which allows a user to carry
out an action. An authorization object can group up to 10 authorization
fields that are checked in an AND relationship.
· For
an authorization check to be successful, all field values of the authorization
object must be maintained accordingly. The fields in an object should not be
seen as input fields on a screen. Instead, fields should be regarded as system
elements, such as infotypes, which are to be protected.
· You
can define as many system access authorizations as you wish for an object by
creating a number of allowed values for the fields in an object. These value
sets are called authorizations. The system checks these authorizations
in OR relationships.
VIRSA FIREFIGHTER INTERVIEW QUESTIONS
1.
What is firefighter? Why it is useful?
2.
What are the types of users available in SPM?
3.
What is the difference between owner and controller?
4.
What are the roles we can assign to different users in
SPM?
5.
What are the tables for firefighter?
6.
How can we configure firefighter id?
7.
How can we assign FFID to firefighter?
8.
What is the background job to generate the report?
9.
How can we get the report of FFID’s assignment?
10.
What are the types of firefighters available?
11.
What are the important parameters that we configure in firefighter
configuration?
12.
How can we generate the reports in FF? What reports can we get
using FF?
13.
Maximum how many days we can give FFID to Fire Fighter?
14.
In what situations we use FFID?
15.
What are the settings we need to do to get the FFID trace details?
Assigning Authorization objects to Users in BI/BW
Assigning Authorization Objects to Users:
# Go to the screen
(RSECADMIN) , and click on assignment button under
user tab:
# Now we can assign the created
Authorization Object to any user using this tool.
# Adding the created Authorization
Object (ZDWKJTEST) to the user ZNBITSRTS. I will be using the same user through
out this blog for running any query so that it can use the restrictions which
are applying using the Authorization Object.
# We can also assign the authorization
to users through role/profile using the standard Authorization Object
S_RS_AUTH:
# User with Authorization Object
0BI_ALL is having full access to data, and can overwrite any other
Authorization Objects assignment to it.
# Query on InfoProvider with
Authorization Objects: Below is the test query in which I added the InfoObject
for which we created the test Authorization Object (ZDWKJTEST).
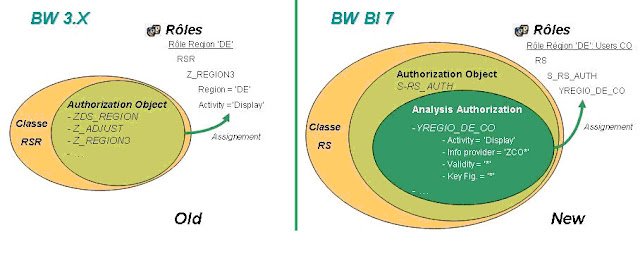
Maintaining Authorizations in BI/BW
SAP BI security is an
integral part of any BI implementation. Integrating all the data coming from
various source systems and providing the data access based on the user’s role
is one of the major concerns of all the BI Projects.
Security of SAP R/3-ECC systems
are based on the activities while SAP BI security is focused on what data user
can access. Security in BI is categorized by major 2 categories:
Administrative
Users – The
way we maintain security for administrative users is same as ECC security but
we have additional authorization objects in system which are defined only for
BI objects.
Reporting Users– We have separate tools(Analysis
Authorization) to maintain security for reporting users.
What is
Authorization Object?
It allows to check whether a
user is allowed to perform a certain action. Actions are defined on the fields,
and each field in authorization object should pass the check. We can check all
the Standard BI Authorization Objects using tcode SU21 under the Business Warehouse
folder:
 With the SAP BI 7.0 we have
new tool to maintain the reporting level security. We can access this new tool
using tcode RSECADMIN
which replaces the old RSSM tool of BW 3.x.
With the SAP BI 7.0 we have
new tool to maintain the reporting level security. We can access this new tool
using tcode RSECADMIN
which replaces the old RSSM tool of BW 3.x.
## Below are the Step-by-Step
instructions to create/maintain authorization objects for SAP BI Reporting:
I am covering the scenario
where each employee (Sales Team) is assigned with one territory number, and the
data should be accessible to employee based on their territory only. For this
scenario to work we have to set security restriction for the corresponding
territory InfoObject (ZDWSLTER).
# The first step before we create any
Authorization Object is to set all the InfoObjects as authorization relevant
for which we want to restrict data access.
Authorization
Objects on InfoObject’s of type Characteristic:
# For accessing the new Analysis
Authorization tools we use tcode RSECADMIN -> Authorizations Tab ->
Maintenance Button
# We can also use tcode RSECAUTH directly to come to
maintenance screen:
# We have to give the technical name
of the Authorization Object (ZDWKJTEST) then hit the create button:
# The very first step of creating any
Authorization Object is to add the special characteristics as field for
restirction:
# The below 3 characteristics are
mandatory for defining any Authorization Object. If we don’t have this we will
get no access to any InforProvider. By default this gives us access to all the
InfoProvider(Full Access), but we can also set the value of InfoProvider for
which we want the Authorization Object to work.
# Now I am adding the infoobject(ZDWSLTER) for which we
want to add restriction
# We can double click on the newly
added infobject, and can define the value which we want to allow for this
InfoObject. We can also set the dynamic value using Customer Exit Code which we
will cover later in this blog.
Authorizations in SAP NW BI
TOPICS
1. MODELING
Difference
between rssm and rsecadmin
RSSM
|
RSECADMIN
|
Old transaction: RSSM Concept of authorization: 'Reporting Authorization' |
New transaction : RSECADMIN Concept of authorization: 'Analysis Authorization' |
Assignement of Reporting
authorization:* by pfcg: mass distribution of auth by using role
|
Assignement of Analysis authorization :* by PFCG: mass distribution of auth by using role, |
Full Authorization:
SAP_ALL, SAP_NEW
|
Full Authorization: SAP_ALL, SAP_NEW |
Modeling:* IO marked as Authorization relevant, |
Modeling:* IO + Navigation ATTR can be Authorization relevant, |
-
|
New object authorization for Web application Designer & Report Designer:* S_RS_BTMP, |
Step by
Step
RSSM
|
RSECADMIN
|
|
0. Pre-requisites
|
-
|
Activate all business content related to authorizations before you get started:* InfoObjects: 0TCA* and 0TCT* Set the following InfoObjects as "authorization relevant":* 0TCAACTVT Add 0TCAIFAREA as an external hierarchy characteristic to 0INFOPROV (optional) |
1. Set Master data
Authorization relevant
|
RSA1 -> InfoObjects
-> Business Explorer Tab -> Flag 'Authorization relevant
|
RSA1 -> InfoObjects -> Business Explorer Tab -> Flag 'Authorization relevant RSA1 -> InfoObjects -> Attribute Tab -> Flag 'AuthorizRelevant' |
2. Create Authorization
Object/ Analysis authorization
|
RSSM -> Enter the
name of your Authorization object -> Create -> Put IO Authorization
relevant in the selected InfoObjects part -> Save
|
|
3. Set Info provider
|
RSSM -> Select:
'Check for Info Cubes' -> Change -> Flag the related Info Cubes
|
|
4. Create BEX variable
for authorization
|
1. Right click on the
IO -> choose 'Restrict'
2. Choose 'Selection' = 'Single Value' and 'from Hierarchy' = 'flat list' If a hierarchy exists, select the hierarchy for the IO 3. Go on the variables tab -> Right click -> 'New variable' 4. For a restriction without hierarchy, the type of variable is 'Characteristic Value' and if you have choose a hierarchy, the type of variable is 'Hierarchy node' 5. Select a variable name & a description 6. Choose 'Processing by': = 'Authorization' then check the characteristic and click 'next' 7. Choose the display area for the variable -> Variable represents: = 'Single Value' or 'Selection Option' 8. Choose if the variable entry is Optional or mandatory, 9. Don't select 'Ready for input' and 'Can be changed in query navigation 10. Next to the end |
|
5. Insert Authorization
in Role
|
||
6. Assign
Authorization/ Role to Users
|
Subscribe to:
Comments (Atom)