TOPICS
1. MODELING
Difference
between rssm and rsecadmin
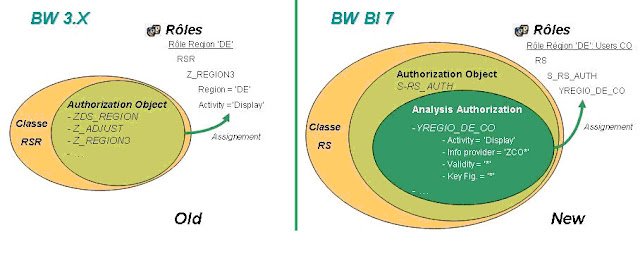
RSSM
|
RSECADMIN
|
Old transaction: RSSM
Concept of authorization: 'Reporting Authorization'
|
New transaction : RSECADMIN
Concept of authorization: 'Analysis Authorization'
|
Assignement of Reporting
authorization:* by pfcg: mass distribution of auth by using role
 by RSSM: generation way (use with Business
Content and flat files loading)
by RSSM: generation way (use with Business
Content and flat files loading)
|
Assignement of Analysis authorization :* by PFCG: mass distribution of
auth by using role,
 by RSECADMIN manual way -> Assignement
-> Auth selection ->Insert,
by RSECADMIN manual way -> Assignement
-> Auth selection ->Insert,
 by RSECADMIN: generation way (use with
Business Content and flat files loading)
by RSECADMIN: generation way (use with
Business Content and flat files loading)
|
Full Authorization:
SAP_ALL, SAP_NEW
|
Full Authorization: SAP_ALL, SAP_NEW
 0BI_ALL: * Allow full authorization
for the IO authorization relevant, 0BI_ALL: * Allow full authorization
for the IO authorization relevant,
 Used in the authorization object: S_RS_AUTH,
Used in the authorization object: S_RS_AUTH,
 Report 'RSEC_GENERATE_BI_ALL' for the SAP_ALL
user,
Report 'RSEC_GENERATE_BI_ALL' for the SAP_ALL
user,
|
Modeling:* IO marked as Authorization relevant,
 rssm enable to flag relevant
infoprovider,
rssm enable to flag relevant
infoprovider,
 rssm are used to custom Auhthorization
object, rssm are used to custom Auhthorization
object,
 Authorization variable are used in Bex Query, Authorization variable are used in Bex Query,
 Pfcg to assign reporting authorization trough
the Object class: RSR, Pfcg to assign reporting authorization trough
the Object class: RSR,
 Query access manage by object S_RS_COMP,
S_RS_COMP1,
Query access manage by object S_RS_COMP,
S_RS_COMP1,
 Area Button/ Access : S_RS_FOLD,
Area Button/ Access : S_RS_FOLD,
 Authorization for Cube, ODS, Hierarchy and
infoset managed by:
Authorization for Cube, ODS, Hierarchy and
infoset managed by:
 S_RS_ICUBE,
S_RS_ICUBE,
 S_RS_ODSO,
S_RS_ODSO,
 S_RS_HIER,
S_RS_HIER,
 S_RS_ISET.
S_RS_ISET.
|
Modeling:* IO + Navigation ATTR can be Authorization relevant,
 An IO auth relevant is auth relevant for all
the cube he is used,
An IO auth relevant is auth relevant for all
the cube he is used,
 rsecadmin to define Analysis
authorization with sepcial IO : 0TCAACTVT, 0TCAIPROV, 0TCAVALID,
rsecadmin to define Analysis
authorization with sepcial IO : 0TCAACTVT, 0TCAIPROV, 0TCAVALID,
 Authorization variable are used in Bex
Query,
Authorization variable are used in Bex
Query,
 pfcg to assign analysis authorization through
the object S_RS_AUTH (Object Class: RS),
pfcg to assign analysis authorization through
the object S_RS_AUTH (Object Class: RS),
 Query access manage by object S_RS_COMP,
S_RS_COMP1,
Query access manage by object S_RS_COMP,
S_RS_COMP1,
 Area Button/ Access : S_RS_FOLD,
Area Button/ Access : S_RS_FOLD,
 Authorization for Cube and ODS for reporting
user are managed by the special authorization characteristic 0TCAIPROV,
Authorization for Cube and ODS for reporting
user are managed by the special authorization characteristic 0TCAIPROV,
 S_RS_ICUBE, S_RS_ODSO, S_RS_HIER, S_RS_ISET:
are not checked anymoe for reporting user.
S_RS_ICUBE, S_RS_ODSO, S_RS_HIER, S_RS_ISET:
are not checked anymoe for reporting user.
|
|
 S_RS_ICUBE, S_RS_ODSO, S_RS_HIER, S_RS_ISET:
are used for allowing access to developper team,
S_RS_ICUBE, S_RS_ODSO, S_RS_HIER, S_RS_ISET:
are used for allowing access to developper team,
 New object to manage acess for developper
user:
New object to manage acess for developper
user:
|
-
|
New object authorization for Web application Designer & Report Designer:*
S_RS_BTMP,
 S_RS_BITM,
S_RS_BITM,
 S_RS_ERPT,
S_RS_ERPT,
 S_RS_EREL.
S_RS_EREL.
|
Step by
Step
|
RSSM
|
RSECADMIN
|
0. Pre-requisites
|
-
|
Activate all business content related to authorizations before you get
started:* InfoObjects: 0TCA* and 0TCT*
 InfoCubes: 0TCA*
InfoCubes: 0TCA*
Set the following InfoObjects as "authorization relevant":*
0TCAACTVT
 0TCAIPROV
0TCAIPROV
 0TCAVALID
0TCAVALID
 0TCAKYFNM (optional, if key figure restriction
needed)
0TCAKYFNM (optional, if key figure restriction
needed)
Add 0TCAIFAREA as an external hierarchy characteristic to 0INFOPROV
(optional)
|
1. Set Master data
Authorization relevant
|
RSA1 -> InfoObjects
-> Business Explorer Tab -> Flag 'Authorization relevant
|
RSA1 -> InfoObjects -> Business Explorer Tab -> Flag 'Authorization
relevant
RSA1 -> InfoObjects -> Attribute Tab -> Flag 'AuthorizRelevant'
|
2. Create Authorization
Object/ Analysis authorization
|
RSSM -> Enter the
name of your Authorization object -> Create -> Put IO Authorization
relevant in the selected InfoObjects part -> Save
|
|
3. Set Info provider
|
RSSM -> Select:
'Check for Info Cubes' -> Change -> Flag the related Info Cubes
|
 The IO authorization relevant are
authorization relevant for all cubes The IO authorization relevant are
authorization relevant for all cubes
|
4. Create BEX variable
for authorization
|
1. Right click on the
IO -> choose 'Restrict'
2. Choose 'Selection' = 'Single Value' and 'from Hierarchy' = 'flat list'
If a hierarchy exists, select the hierarchy for the IO
3. Go on the variables tab -> Right click -> 'New variable'
4. For a restriction without hierarchy, the type of variable is
'Characteristic Value' and if you have choose a hierarchy, the type of
variable is 'Hierarchy node'
5. Select a variable name & a description
6. Choose 'Processing by': = 'Authorization' then check the characteristic
and click 'next'
7. Choose the display area for the variable -> Variable represents: =
'Single Value' or 'Selection Option'
8. Choose if the variable entry is Optional or mandatory,
9. Don't select 'Ready for input' and 'Can be changed in query navigation
10. Next to the end
|
|
5. Insert Authorization
in Role
|
|
|
6. Assign
Authorization/ Role to Users
|
|
|
 Reporting User: Authorization for End User
Reporting User: Authorization for End User
 S_RS_AUTH:
S_RS_AUTH:
 Insert here the Analysis Authorization you
customize in Rsecadmin.
Insert here the Analysis Authorization you
customize in Rsecadmin.
 Allow right on IO marked as 'authorization
relevant' (Data)
Allow right on IO marked as 'authorization
relevant' (Data)
 S_RS_COMP : Query Accessibility
S_RS_COMP : Query Accessibility
 Activity: 01 (Create or generate), 02 (Change),
03 (Display), 06 (Delete), 16 (Execute), 22 (Enter, Include, Assign)
Activity: 01 (Create or generate), 02 (Change),
03 (Display), 06 (Delete), 16 (Execute), 22 (Enter, Include, Assign)
 InfoArea: '*'
InfoArea: '*'
 InfoCube: <Selected infoprovider>
InfoCube: <Selected infoprovider>
 Name (ID) of a reporting component:
<Selected query>
Name (ID) of a reporting component:
<Selected query>
 Type of a reporting component: CKF (Calculated
key figure), QVW (Query View), REP (Query), RKF (Restricted key figure), SOB
(Selection object, New object !!!), STR (Template structure), VAR (Variable)
Type of a reporting component: CKF (Calculated
key figure), QVW (Query View), REP (Query), RKF (Restricted key figure), SOB
(Selection object, New object !!!), STR (Template structure), VAR (Variable)
 S_RS_COMP1 : Query for specific users
S_RS_COMP1 : Query for specific users
 S_RS_FOLD ( Hide 'Folder' Pushbutton): 'False'
or 'True'
S_RS_FOLD ( Hide 'Folder' Pushbutton): 'False'
or 'True'
 S_USER_AGR: Role Name
S_USER_AGR: Role Name
 S_RS_BITM : !!! NEW !!!
S_RS_BITM : !!! NEW !!!
 S_RS_BTMP : !!! NEW !!!
S_RS_BTMP : !!! NEW !!!
 Developper
Developper
 S_DEVELOP
S_DEVELOP
 S_RO_BCTRA -in ECC side for activate (remote)
Datasource
S_RO_BCTRA -in ECC side for activate (remote)
Datasource
 S_RS_BC
S_RS_BC
 S_RS_BCS
S_RS_BCS
 S_GUI
S_GUI
 S_RS_DS: Authorizations for working with the
DataSource or its sub-objects (as of SAP NetWeaver 2004s)
S_RS_DS: Authorizations for working with the
DataSource or its sub-objects (as of SAP NetWeaver 2004s)
 S_RS_ISNEW: Authorizations for working with new
InfoSources or their subobjects (as of SAP NetWeaver 2004s)
S_RS_ISNEW: Authorizations for working with new
InfoSources or their subobjects (as of SAP NetWeaver 2004s)
 S_RS_DTP: Authorizations for working with the
data transfer process and its subobjects
S_RS_DTP: Authorizations for working with the
data transfer process and its subobjects
 S_RS_TR: Authorizations for working with
transformation rules and their subobjects
S_RS_TR: Authorizations for working with
transformation rules and their subobjects
 S_RS_CTT: Authorizations for working with
currency translation types
S_RS_CTT: Authorizations for working with
currency translation types
 S_RS_UOM: Authorizations for working with
quantity conversion types
S_RS_UOM: Authorizations for working with
quantity conversion types
 S_RS_THJT: Authorizations for working with key
date derivation types
S_RS_THJT: Authorizations for working with key
date derivation types
 S_RS_PLENQ: Authorizations for maintaining or
displaying the lock settings
S_RS_PLENQ: Authorizations for maintaining or
displaying the lock settings
 S_RS_RST: Authorization object for the RS trace
tool
S_RS_RST: Authorization object for the RS trace
tool
 S_RS_PC: Authorizations for working with
process chains
S_RS_PC: Authorizations for working with
process chains
 S_RS_OHDEST: Open Hub Destination
S_RS_OHDEST: Open Hub Destination
 S_RS_DAS: Authorizations for working with Data
Access Services
S_RS_DAS: Authorizations for working with Data
Access Services
 S_RS_BTMP: Authorizations for working with BEx
Web templates
S_RS_BTMP: Authorizations for working with BEx
Web templates
 S_RS_BEXTX: Authorizations for the maintenance
of BEx texts Authorization objects for the administration of analysis
authorizations
S_RS_BEXTX: Authorizations for the maintenance
of BEx texts Authorization objects for the administration of analysis
authorizations
 S_RSEC: Authorization for assignment and
administration of analysis authorizations
S_RSEC: Authorization for assignment and
administration of analysis authorizations
 S_RS_AUTH: Authorization object to include
analysis authorizations in roles
S_RS_AUTH: Authorization object to include
analysis authorizations in roles
 S_RS_ADMWB: Changed Authorization Objects (Data
Warehousing Workbench: Objects)
S_RS_ADMWB: Changed Authorization Objects (Data
Warehousing Workbench: Objects)
 General
General
 S_RFC: Authorization Check for RFC Access:
S_RFC: Authorization Check for RFC Access:
 Activity 16
Activity 16
 Name of RFC to be protected *
Name of RFC to be protected *
 Type of RFC object to be protetected: FUGR
Type of RFC object to be protetected: FUGR
 S_TCODE: Transaction Code Check at Transaction
Start
S_TCODE: Transaction Code Check at Transaction
Start
 Transaction Code SE37,RRMX, RRMXP
Transaction Code SE37,RRMX, RRMXP
 S_GUI: Authorization for GUI activities
S_GUI: Authorization for GUI activities
 Activity 02, 60, 61
Activity 02, 60, 61
 S_BDS_DBC-SRV-KPR-BDS: Authorizations for
Accessing Documents
S_BDS_DBC-SRV-KPR-BDS: Authorizations for
Accessing Documents
 Activity 03
Activity 03
 BDS: Data element for LOIO cla *
BDS: Data element for LOIO cla *
 Generation (rsecadmin)
Generation (rsecadmin)
 Role (pfcg)
Role (pfcg)
 Tables
Tables
 RSECVAL : Authorization Value Status,
RSECVAL : Authorization Value Status,
 RSECUSERAUTH : BI AS Authorizations:
Assignment of User Auth.
RSECUSERAUTH : BI AS Authorizations:
Assignment of User Auth.
 Function Modules:
Function Modules:
 RSEC_AUTHORITY_CHECK_IPROV
RSEC_AUTHORITY_CHECK_IPROV
 RSEC_AUTH_GET_IOBJ_RELEVANT
RSEC_AUTH_GET_IOBJ_RELEVANT
 RSEC_CHECK_IPROV
RSEC_CHECK_IPROV
 RSEC_CHECK_VALIDITY
RSEC_CHECK_VALIDITY
 RSEC_COMPLETE_HIERAUTH
RSEC_COMPLETE_HIERAUTH
 RSEC_GET_AUTH_FOR_USER
RSEC_GET_AUTH_FOR_USER
 RSEC_GET_AUTH_HIER_FOR_USER
RSEC_GET_AUTH_HIER_FOR_USER
 RSEC_ASSIGN_AUTHS_TO_USERS
RSEC_ASSIGN_AUTHS_TO_USERS
 RSEC_GET_ALL_GENERATED_AUTHS
RSEC_GET_ALL_GENERATED_AUTHS
 RSEC_READ_ODS_HIER
RSEC_READ_ODS_HIER
 RSEC_READ_ODS_USER_AUTH
RSEC_READ_ODS_USER_AUTH
 RSEC_READ_ODS_VAL
RSEC_READ_ODS_VAL
 RSEC_AUTHORIZATIONS_OF_USER
RSEC_AUTHORIZATIONS_OF_USER
 RSEC_GET_AUTH_FOR_USER_RFC
RSEC_GET_AUTH_FOR_USER_RFC


this is an excellent info..keep it up..thanQ somuch
ReplyDeleteThank you. It is such a wonderful post. it has great information it is very useful for sap hana videos.
ReplyDeleteIt was so nice article.I was really satisfied by seeing this article sap wm training videos.
ReplyDeleteI am glad that I saw this post. It is informative blog for us and we need this type of blog thanks for share this blog, Keep posting such instructional blogs and I am looking forward for your future posts.
ReplyDeleteCyber Security Projects for CSE
JavaScript Training in Chennai
Project Centers in Chennai for CSE
JavaScript Training in Chennai